Building Safe Anonymous Mail Module – Project journey with Aztec

Introduction to SAMM and its Vision
The Safe Anonymous Mail Module (SAMM) is a original privacy-focused solution for multisig wallets, born from our pursuit of secure and anonymous Web3 communication. Developed atop the Safe Anonymization Module (SAM), SAMM extends that foundation with email-based private multisignature functionality powered by zero-knowledge proofs in Aztec’s Noir language. In essence, SAMM allows Safe wallet transactions to be managed via familiar email interfaces, all while preserving the anonymity of the Safe’s participants through advanced cryptography. This work was made possible by generous grant support from the Aztec Foundation, aligning with the broader Web3 goal of enabling secure, user-friendly, and privacy-preserving decentralized applications.
We at Oxorio are grateful to Aztec Foundation for backing this vision, as well as to audit teams of Nethermind and OpenZeppelin, who helped ensure we built SAMM with the highest standards of diligence and security.
From Safe Anonymization Module to Email-Powered Privacy
SAMM’s development journey began with our earlier Safe Anonymization Module (SAM), a Safe Wallet plugin conceived under a SafeDAO grant to anonymize multisig approvals using zk-SNARK technology. SAM proved that multisig transactions could be confirmed without revealing which owner approved them, this fueled our ambition to push the concept even further. We envisioned an intuitive way for multisig stakeholders to participate using something as simple as email, without sacrificing privacy. With the Aztec Foundation’s support, we embarked on implementing the zkEmail concept for Safe: allowing multisig owners to approve transactions by email, secured by Noir-based zero-knowledge circuits. This approach combines the convenience of email communication with the rigor of Zero-Knowledge proof security, effectively building email-driven multisigs that keep participant identities hidden.
The grants enabled us to plan a two-milestone roadmap, and we’re proud to report that both milestones were delivered successfully. In Milestone 1, we built out the core SAMM smart contracts and Noir circuits, demonstrating a working prototype for anonymous Safe control via email. By Milestone 2, we had completed an end-to-end integration with a web UI and relayer service, producing a functional system ready for real-world testing. Each phase of the project was documented in detailed reports and technical specs, from the initial grant proposal through to final deliverables – all of which we have made publicly available for the community’s reference. (See the links to our grant application, technical specification, and milestone reports in the References below.)
Technical Architecture and Implementation
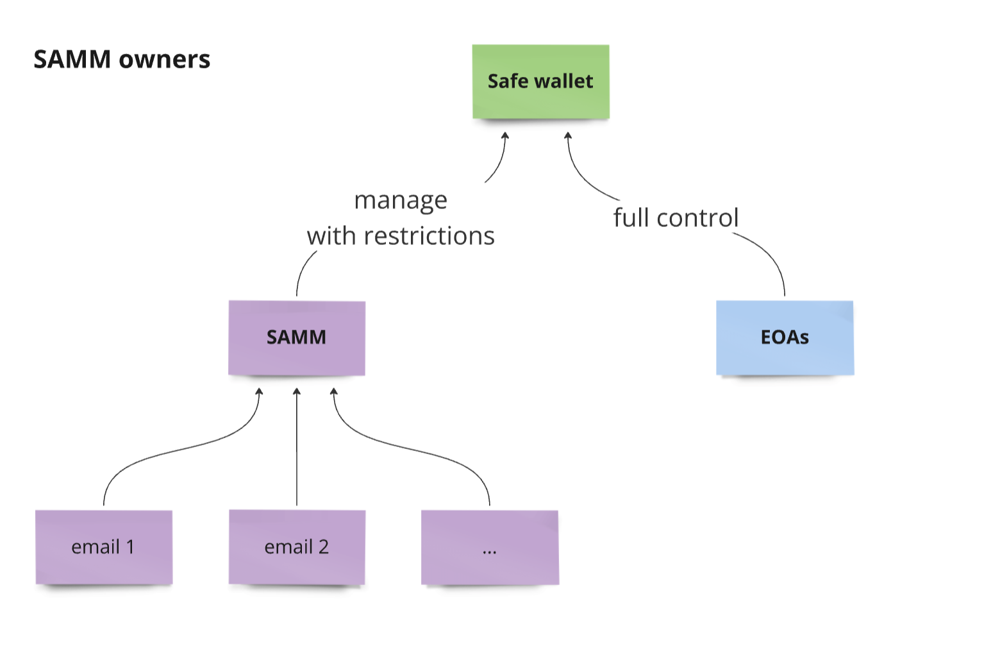
SAMM’s architecture builds on the Safe module system: EOA owners retain full control of the Safe, while the SAMM module (with its list of authorized email identities) can manage routine transactions under strict security policies. At a high level, SAMM integrates several components to deliver seamless yet anonymous multisig management:
- Safe Module Smart Contracts:
The SAMM smart contract (an upgradable Safe module) acts as the on-chain gatekeeper. It enforces which actions the module can perform on the Safe and stores a Merkle tree commitment of authorized participant email addresses. The module can be installed on any Safe wallet via the standard enableModule call, after being deployed through a factory contract. We used Solidity and the Foundry framework to implement these contracts, ensuring compatibility with the existing Safe{Core} protocol. Notably, the module is designed with security restrictions – for example, SAMM cannot alter Safe owners or perform arbitrary calls outside a predefined scope – so the Safe’s critical configurations remain protected. This allows everyday transactions to be handled anonymously by SAMM, while extraordinary actions still require the original Safe owners (EOAs).
- Zero-Knowledge Circuits in Noir:
At the heart of SAMM’s privacy lies a set of custom Noir circuits (replacing our earlier Circom circuits from the SAM project). These circuits generate zk-SNARK proofs that validate email-based approvals without revealing which email (and by extension, which Safe owner) signed off. Specifically, every time a participant emails an approval, a ZK proof is produced to confirm: (a) the sender’s email is indeed one of the authorized addresses in the module’s Merkle tree, (b) the email’s recipient is the trusted SAMM relayer service, (c) the email contains the correct transaction ID in its header, and (d) a valid DKIM signature is present, proving the email’s authenticity. By verifying these conditions in zero-knowledge, SAMM ensures that on-chain it is only known that some authorized owners approved a transaction – meeting the required threshold – but not which ones. We leveraged Aztec’s Noir language for these circuits due to its developer-friendly syntax and efficient proving backend. The Noir circuits implement logic inspired by the zkMail architecture (notably from the emailwallet.org concept) adapted to Safe’s multisig context. For example, we included Noir implementations of signature verification (edDSA for DKIM and Ethereum’s secp256k1 for Safe owners) and Merkle proofs for email inclusion. The circuits are open-sourced in our repository, and we’ve provided documentation on how to compile and test them using the Aztec Noir toolkit.
- Relayer and Backend Services:
To bridge the off-chain email world with on-chain execution, SAMM relies on a Relayer backend. The relayer is an off-chain service (we built a prototype in Python, drawing on existing open-source email wallet relayer code) that monitors a dedicated email inbox for incoming messages from SAMM participants. When an email arrives, the relayer parses it for a transaction command or approval response and triggers the Noir prover service. A zk proof is generated for the email, as described above, using the participant’s secret keys. If the Safe’s signature threshold is, say, 2 of 3, the relayer will collect proofs from multiple independent emails. Once the threshold number of valid proofs is gathered, the relayer submits the batch of proofs to the SAMM smart contract on Ethereum. (If not enough approvals are received, the proofs remain in an off-chain database and no transaction is executed.) The SAMM contract, upon receiving the proofs, verifies them using on-chain proof verification (via the Noir verifier contract) and then executes the proposed Safe transaction if and only if the proofs are valid and quorum is met. This architecture ensures the transaction details and outcomes are public (a requirement of executing on Ethereum), but the identities of approving owners stay hidden behind the zk-SNARK proofs. The backend stack also includes a simple SMTP server or integration for receiving emails, a Prover service (which could be a separate microservice for generating/verifying proofs, isolated for security), and a database (PostgreSQL) for storing module state like pending proposals and partially collected approvals. We also set up a TheGraph subgraph to index on-chain events from the SAMM module, enabling the UI to easily fetch the status of proposals and executed transactions.
- User Interface (Safe App):
To make SAMM accessible and user-friendly, we built a front-end as a Safe App (React/Next.js based) that can plug into the Safe wallet interface. This web UI allows Safe owners to deploy and configure the SAMM module through a few clicks – for example, specifying the list of participant email addresses and the required threshold (all of which get hashed into the Merkle root used by the contract). The UI also provides a dashboard for monitoring proposals and approvals in real time. Users can see pending transactions, which participants have (anonymously) responded, and when a transaction has enough proofs to be executed. For security, sensitive operations like changing module parameters still require traditional Safe owner confirmations through the Safe interface, but SAMM’s UI guides users through generating the necessary Safe transactions for such changes. We implemented the UI using the Safe App SDK, ensuring it could be loaded alongside other Safe apps. Under the hood, the front-end communicates with the relayer backend (for example, to initiate a module setup or query proof statuses) via a REST API. The UI’s code is open-source and included in our repositories, alongside instructions so developers can run their own instance or even integrate SAMM’s functionality into other interfaces.
- Technology Stack in Summary:
Our implementation is multi-faceted, leveraging the right tools for each layer. On the smart contract side, Solidity with Foundry was used for Safe module development. For zero-knowledge, Aztec’s Noir DSL drives the circuit logic and proof generation. The backend services were prototyped in Python (benefiting from existing email handling libraries and Noir SDK bindings), though a Rust implementation is conceivable for production performance. The front-end is built with React/TypeScript (Next.js), integrated into the Safe{Wallet} as a plugin app. All components are designed to be deployable by the community – for instance, the relayer can be self-hosted and pointed to a custom email server if desired, reflecting a decentralized ethos where no central party must be trusted (aside from relying on standard email providers’ security for delivering signed emails).
Security Audits and Diligence
Oxorio’s background as a web3 auditing firm made security our top priority from day one – every design choice was made with careful consideration of potential attack vectors. Engagement of professional third-party auditors for rigorous review of SAMM’s contracts and infrastructure was made possible with support from Aztec Foundation as part of the grant privilege. OpenZeppelin performed an in-depth audit of the SAMM smart contracts, examining the module’s Solidity code and its integration with the Safe wallet for any flaws. In parallel, Nethermind’s security team audited the broader system including the Noir circuits and backend components. This approach provided excellent security coverage: OpenZeppelin’s expertise in Ethereum security and Nethermind’s knowledge of ZK applications together helped validate our approach from all angles. The audits scrutinized everything from cryptographic correctness of the proofs, to contract upgradeability and access control, to the email relay logic. Minor issues and optimizations identified by the auditors were promptly addressed, and the final audit results indicated that SAMM meets a high security standard with no critical vulnerabilities remaining. We want to thank both OpenZeppelin and Nethermind for their thorough and professional work – their seal of approval gives the community confidence in deploying SAMM in real-world scenarios. Moreover, the auditing process confirms our commitment to diligence and Oxorio’s dedication to building secure Web3 infrastructure. (For transparency, audit reports are availabel in SAMM GitHub repository linked below).
Open-Source Code and Community Collaboration
From the very start, SAMM was built as an open-source project – we believe that community collaboration is crucial for security tools, especially ones centered on privacy. All of SAMM’s code is publicly available under permissive licenses in our GitHub organization. This includes separate repositories for each major component: the SAMM smart contracts (Solidity code and tests), the SAMM Noir circuits, the backend relayer service, and the Safe App frontend. We’ve also published a comprehensive technical specification and developer guides (initially drafted as part of our grant documentation) to help others understand and use the module. As of this writing, the SAMM codebase comprises dozens of commits across these repos, with contributions from multiple Oxorio engineers. For example, our Noir implementation of the MiMC Sponge hash (for Merkle trees) and the DKIM verification logic can serve as starting points for other zk applications. We encourage developers to explore the code, run the tests, and deploy their own instance of SAMM on a testnet. To facilitate this, our README documents provide step-by-step instructions for setup, and we’ve deployed a live demo of the SAMM Safe App for anyone to try with a sample Safe. Community feedback is extremely valuable – whether it’s in the form of GitHub issues, pull requests, or discussions – and will guide the future of the project. Open-source also means transparency: the community can audit the code themselves and suggest improvements, further strengthening the module’s security over time. By releasing SAMM openly, we hope to seed a whole ecosystem of privacy-preserving Safe modules and inspire others to build on our approach.
Future Roadmap and Aspirations
Looking ahead, we have a number of directions in mind – and we invite the Safe, Safe Builders ecosystem, and broader Web3 communities to join us in shaping these next steps. First and foremost, we aspire to see SAMM adopted in real-world use by DAO multisigs and Web3 startups. To that end, we plan to work with early adopters to pilot SAMM in controlled environments (e.g. for DAO treasury approvals or internal governance decisions) and gather feedback on the user experience. On the technical front, one future improvement is enhancing the trustlessness of the relayer: currently the relayer is an off-chain component that users must either run themselves or trust Oxorio’s instance. We envision a community-run network of relayers or a decentralized mechanism (perhaps leveraging specialized email-to-chain oracles) so that no single party is critical. We’re also exploring support for additional message channels beyond traditional email. The core concept of zkAuthenticated approvals could be extended to messaging apps or decentralized communication protocols. Imagine Safe owners approving transactions via a secure chat bot or a mobile app, with a ZK proof generated on the phone – the possibilities are vast, and the email architecture we built is just one template. From a features standpoint, some aspirational upgrades include: implementing rate-limiting or spam protection on the relayer, and providing more granular privacy settings (for instance, proving an owner’s approval anonymously but optionally revealing it to a predefined auditor for compliance purposes). All these ideas come directly from the “Future Steps” we outlined in our Milestone 2 report, and they are framed as open-ended opportunities for the community. We deliberately see SAMM not as a finished product, but as a starting point – a demonstration that anonymous multisig management is feasible. The road ahead will be about refining this concept into a robust, widely-used tool in the Safe ecosystem. We hope to collaborate with SafeDAO and perhaps see SAMM (or a variant of it) eventually become an official Safe module that any Safe user can enable with one click. In the meantime, our team will continue to maintain the project, and we welcome community contributions to drive it forward.
Conclusion and Call to Action
The development of SAMM has been a rewarding journey at the intersection of smart contract security and zero-knowledge innovation. With the backing of Aztec Foundation we transformed an ambitious idea – controlling multisig wallets privately via email – into a working open-source solution. We are proud to have contributed to advancing decentralised security and privacy in Web3, providing building block for others to leverage in their own projects, and for non-technical users to participate in secure blockchain operations without exposing their identities.
Wrapping up this chapter of development, we extend our heartfelt thanks to the Aztec Foundation for their support and trust in this project, to Nethermind and OpenZeppelin for professional excellence in security matters. We encourage developers, auditors, Safe users, and privacy enthusiasts to dive into our codebase, experiment with SAMM, and contribute feedback or improvements. Oxorio will continue to be actively involved, pushing the boundaries of what’s possible with secure, anonymous communication in Web3.
Explore the documentation and code:
Github Repositories:
Audit Reports:
At Oxorio, we specialize in smart contract audits and ZK solutions, helping projects identify critical vulnerabilities before they become costly exploits. Whether you’re preparing for mainnet launch or scaling a ZK-based protocol, our experienced team is here to ensure your code is secure and production-ready. To work with us please reach out to ping@oxor.io, or Telegram us at @oxorio_bizdev or visit https://oxor.io to request an audit.
Contents
YOU MAY ALSO LIKE

What’s wrong with ERC20Permit?
Research
Explore our detailed analysis of the ERC20Permit vulnerability affecting top DeFi protocols. Learn about its impact, mitigation strategies, and how to secure your blockchain projects.
Review of Open Research Problems in Rollup Design
Research
Uncover unresolved challenges in rollup architecture design, shaping the future of Layer 2 solutions in blockchain technology.

Securing Layer 2: Unique Security Concerns and Mitigation Strategies
Research
Explore the unique security challenges of Layer 2 blockchain solutions and learn about OXORIO's specialized strategies for mitigating risks in smart contracts and zk audits.
Have a question?

Stay Connected with OXORIO
We're here to help and guide you through any inquiries you might have about blockchain security and audits.